In the 2026 enterprise landscape, security can no longer be a “checkpoint” at the end of a release cycle. To achieve true innovation velocity, security must be baked into the platform itself. At Buoyant Cloud, we advocate for the “Golden Gate”—a highly automated, declarative pipeline where compliance is invisible but omnipresent.
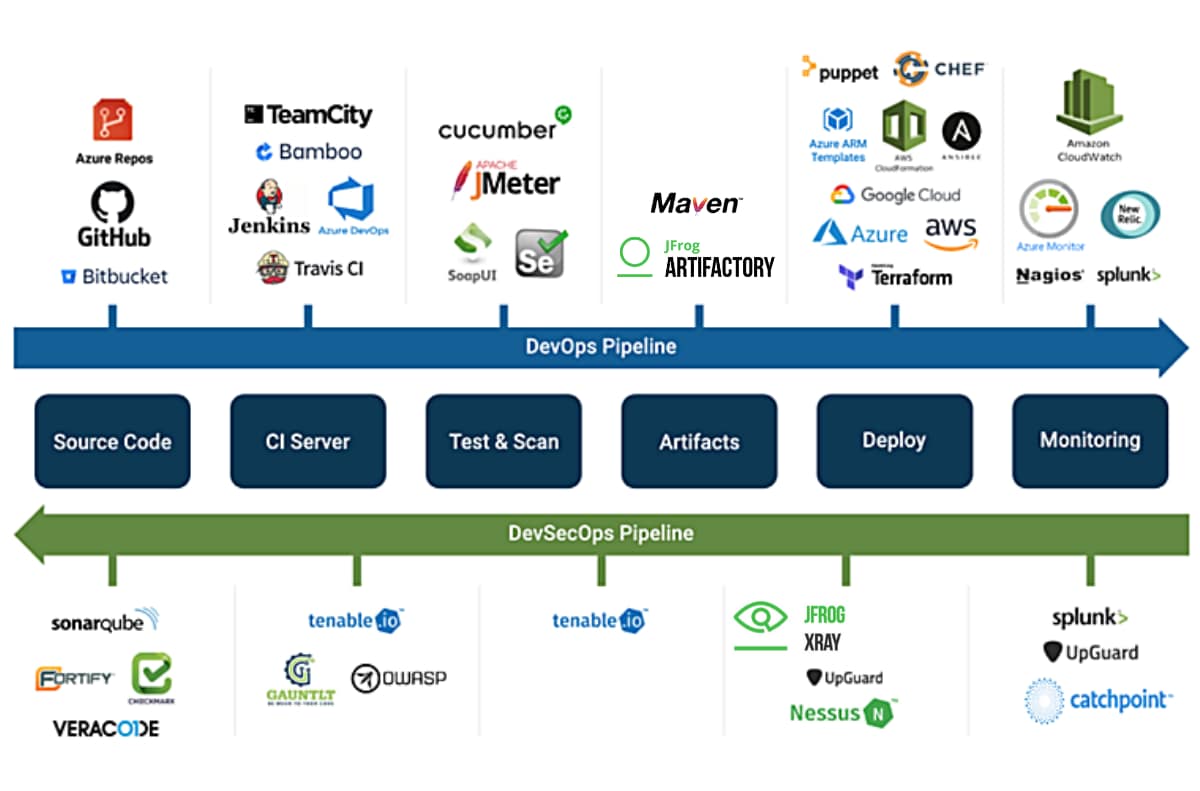
Below is the architectural blueprint for implementing a 9-pillar DevSecOps framework on Google Cloud Platform (GCP).
Sequence: Pre-Commit / Pull Request
The goal is to prevent vulnerabilities from ever entering the repository.
Secret Scanning: Implement tools like TruffleHog or GitHub Advanced Security to detect hardcoded API keys and tokens.
SAST & SCA: Use Semgrep for static analysis and Snyk for dependency scanning to block libraries with known CVEs or risky licenses.
Output: Real-time PR feedback with a “Blocked” status for high-risk findings.
Sequence: CI Pipeline / Merge Gate
Codify your regulatory manual into automated “Law.”
Policy as Code (PaC): Use Open Policy Agent (OPA) with Rego to verify that GKE resources have CPU/RAM limits and reside in the correct geo-regions.
Automated Audit Trails: Stream pipeline events via Fluent Bit to Splunk/ELK for a permanent, tamper-proof record of “who merged what and when.”
Sequence: Build / Artifact Creation
Prove the integrity of your software “ingredients” to mitigate zero-day risks.
SBOM Generation: Create machine-readable CycloneDX inventories for every build.
Binary Authorization: Use Cosign to sign container images. Configure GCP Binary Authorization to only allow signed “Golden Images” to run in production.
Sequence: Pre-Deployment
Eliminate “Snowflake” environments and configuration drift.
Infrastructure as Code: Define all networking and databases via Terraform.
IaC Scanning: Implement Checkov or Terrascan to scan Terraform plans for misconfigurations (e.g., public buckets) before the apply phase.
Sequence: Post-Deployment (Staging)
Test behavior in a live-like environment.
DAST: Run automated “Hack” simulations using OWASP ZAP or StackHawk against running endpoints.
Output: A runtime security report that must be clean before Production approval.
Sequence: Production Deployment
Ensure no system has permanent “God Mode” access.
Secret Management: Inject credentials from HashiCorp Vault or GCP Secret Manager directly into memory.
mTLS: Deploy a Service Mesh (Istio) to enforce encrypted-in-transit communication between microservices.
Sequence: Production Gate
Automate the “bureaucracy” of enterprise compliance.
ITSM Integration: Automatically open and close ServiceNow tickets by attaching the SBOM, scan results, and approval logs as evidence.
Output: A fully closed, audit-ready Change Request (CR) record.
Sequence: Production Rollout
Protect uptime and customer data integrity.
Canary Deployments: Use ArgoCD or Google Cloud Deploy to route 5% of traffic to the new version.
Automated Rollback: If error rates exceed 1%, the pipeline automatically restores the previous stable version.
Sequence: Continuous Operations
Proactive threat detection post-release.
Log Aggregation: Centralize logs in Google Cloud Operations.
AIOps Alerts: Use ML to baseline “normal” behavior and alert on anomalies like unusual data egress or login spikes.
| Pillar | Pipeline Phase | Key Tools |
| 1. Quality | Pre-Commit / PR | GitHub Advanced Security, Snyk, Semgrep |
| 2. Policy | CI Pipeline | OPA (Rego), Fluent Bit, Splunk |
| 3. Materials | Build | Syft, Cosign, Google Binary Auth |
| 4. Foundation | Pre-Deploy | Terraform, Checkov, Terrascan |
| 5. Runtime | Post-Deploy | OWASP ZAP, StackHawk |
| 6. Vault | Runtime | HashiCorp Vault, Istio, WIF |
| 7. Process | Prod Gate | ServiceNow, Jira Service Management |
| 8. Release | Prod Rollout | ArgoCD, Google Cloud Deploy |
| 9. Eyes | Operations | Datadog, Google Cloud Operations |
We track the health of your DevSecOps implementation using these four benchmarks:
Deployment Frequency: Goal: Daily or Weekly.
Lead Time for Changes: Goal: < 4 hours from commit to prod.
Change Failure Rate: Goal: < 5%.
Time to Restore (MTTR): Goal: < 1 hour.
To scale this across an enterprise, we implement a Platform-First strategy:
Standardized App Templates: Pre-configured GKE/Cloud Run repos with GH Workflows and Workload Identity Federation (WIF).
Self-Hosted Runners: Using Actions Runner Controller (ARC) on GKE for secure, internal-only execution.
IDP Scaffolding: An Internal Developer Platform that provides Terraform blueprints for developers.
Ready to Implement a Secure “Golden Gate” Pipeline?
Stop choosing between speed and security. Partner with a Principal GCP Architect to implement a robust DevSecOps framework tailored for North American enterprise scale.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |